Leaderboard
Popular Content
Showing content with the highest reputation on 07/02/2020 in Posts
-
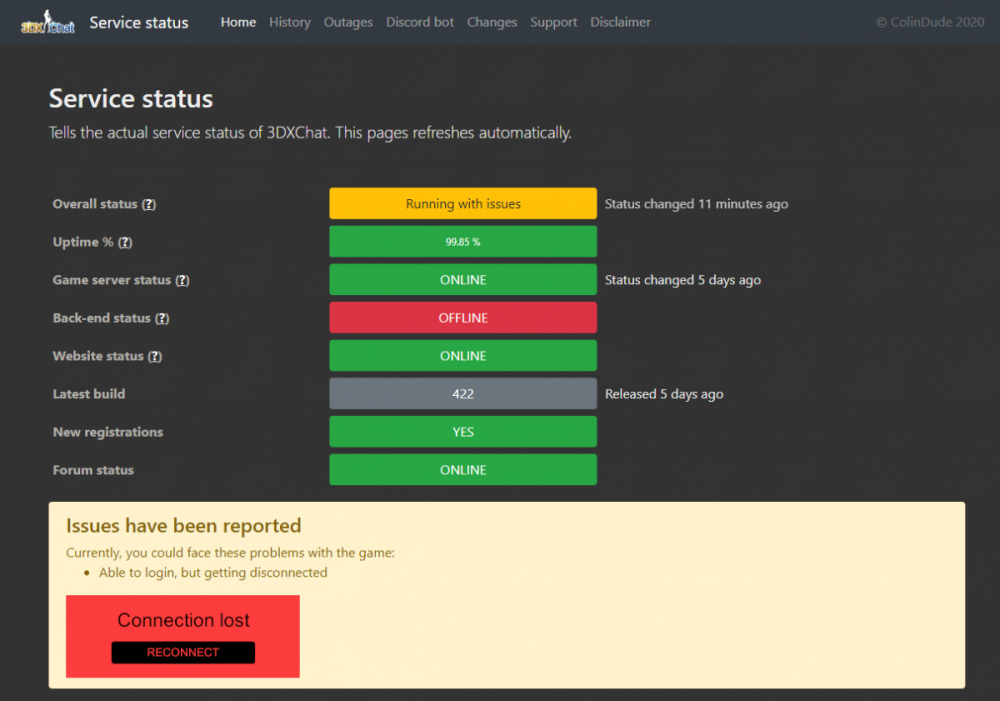
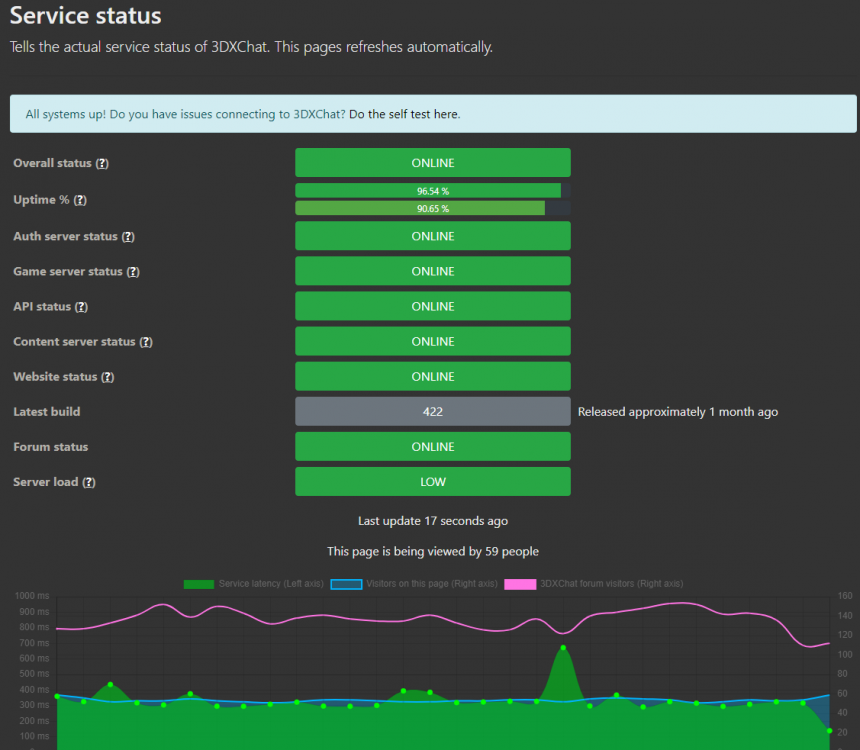
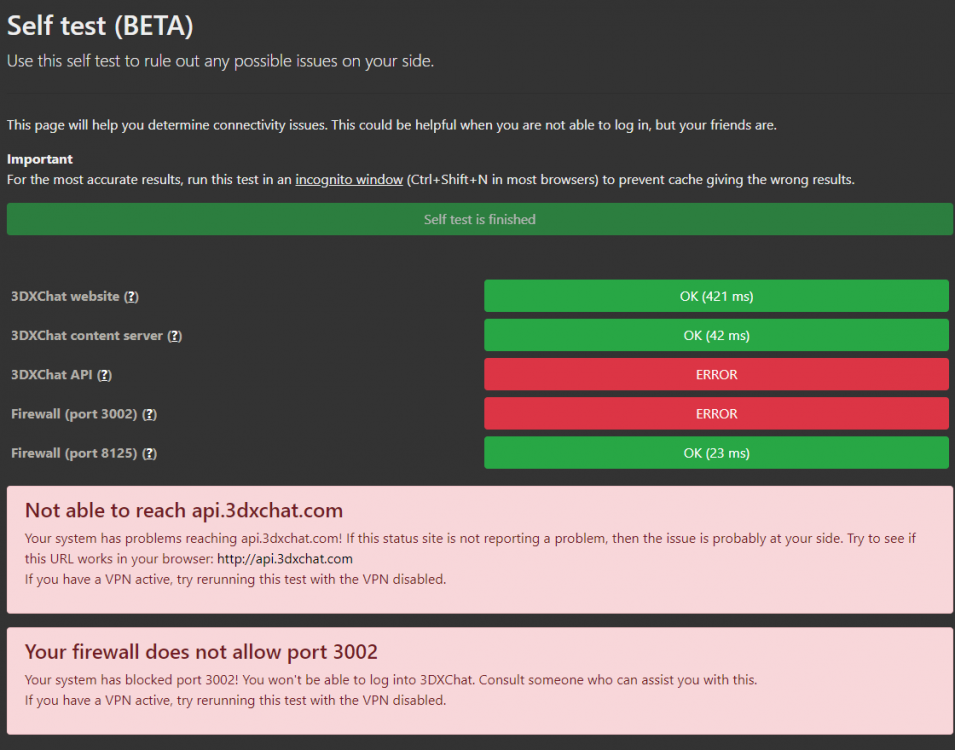
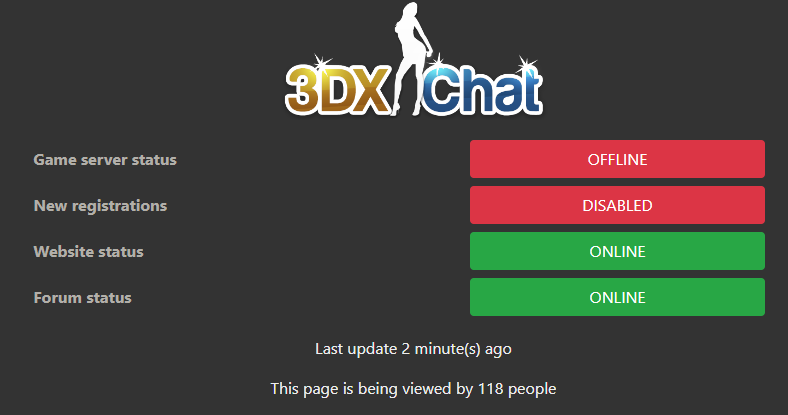
I created a status website for the 3DXChat servers. It automatically updates every 5 minutes, and it'll tell you the actual server status without the hassle. @Gizmo I hope you're OK with this. I ping the game server once every 5 minutes, from one central point. If you're not OK with it I'll take it offline. But I thought it could be helpful for all the users. Check it out here: https://status.3dxchat.net/29 points
-

Build 420 (Test Server)
BillyBigWilly and 18 others reacted to Lisa for a topic
We made fixes. The server is running. Let's test it19 points -

Build 420 (Test Server)
BillyBigWilly and 12 others reacted to Lisa for a topic
Known Issues: - Profiles issue (double click "My Profile" to fix it); - In rare cases, the login window may block you for 15 minutes; - Not all users who receive compensation have the opportunity to enter the game; - The ignore function does not work; - Incorrect display of colors in the chat; - Radio; - Incorrect display of clothes when leaving a closed room.13 points -
We will inform you about the server launch. This utility does not display the real situation, but it looks cool9 points
-
So I work in tech, and am a systems administrator. Granted, for websites, not games, but, puts me in a better understanding than most for this particular problem. Anyway, DDoS attacks are incredibly hard to fight. So here's the thing with DDoS attacks, what happens is hackers infect random peoples PCs with a virus. Maybe the virus doesn't even seem to have any ill effects on the user. Just sits there (often times they throw plenty of other nasty things in there, but, lets keep it simple for now). So now, you have control of thousands of computers under your control, all that are real, have network histories with the ISPs, are on multiple ISPs, all over the world. Now you point them at a server or domain. You hit it with a request that looks somewhat legit. Maybe a login request, or a general ping to see if the server is up (something the game would normally do). Now, you just do that again, and again, and again. You stagger it though. You have 10,000 PCs in your botnet, but not all 10,000 are making requests every second. Say you have 1,000, and they hit a few times in a second. Then they take a break, and swap to the next 1000 and so on. This keeps individual IP addresses from being flagged as trying to access too much, while still flooding the server. So, they're making legit requests to the server the game would make. The question is, how do you filter out the bad traffic? The short answer is, you can't. The long answer involves a LOT of analysis, trying to figure out the IP addresses, what requests they're making, looking for patterns to filter them out (there are programs to assist with this). Now, the other thing to consider is, if you're the hacker, and you're starting to get IPs that are getting blocked, you retire them and get other computers on your botnet. So, ideally, you have something that gives a fake reply to the IPs so the hackers are none the wiser (or at least slow them down). This can be very difficult and much easier said than done. There is no way to 100% filter out DDoS traffic without false positives. It's going to be glitchy for people. What do they need? New data center will help, but it's not a matter of anything physically different, it's a matter of support. They need to either move to a datacenter that offers high level support for DDoS and experience with it, or, hire a company that specializes in it, and give access to firewalls. Not knowing their architecture, my advice would be, move to the cloud with load balancers and a distributed solution. Be able to spawn up more servers when needed, and take advantage of Amazon AWS or Microsoft Azure tools as well as hire a company experienced with DDoS attacks7 points
-

Understanding what a DDOS attack is, and understanding mitigation isnt always easy
AuanaTuutoLC and 5 others reacted to Monique/Aurora for a topic
What is DDoS mitigation? DDoS mitigation refers to the process of successfully protecting a targeted server or network from a distributed denial-of-service (DDoS) attack. By utilizing specially designed network equipment or a cloud-based protection service, a targeted victim is able to mitigate the incoming threat. There are 4 stages of mitigating a DDoS attack using a cloud-based provider: Detection - in order to stop a distributed attack, a website needs to be able to distinguish an attack from a high volume of normal traffic. If a product release or other announcement has a website swamped with legitimate new visitors, the last thing the site wants to do is throttle them or otherwise stop them from viewing the content of the website. IP reputation, common attack patterns, and previous data assist in proper detection. Response - in this step, the DDoS protection network responds to an incoming identified threat by intelligently dropping malicious bot traffic, and absorbing the rest of the traffic. Using WAF page rules for application layer (L7) attacks, or another filtration process to handle lower level (L3/L4) attacks such as memcached or NTP amplification, a network is able to mitigate the attempt at disruption. Routing - By intelligently routing traffic, an effective DDoS mitigation solution will break the remaining traffic into manageable chunks preventing denial-of-service. Adaptation - A good network analyzes traffic for patterns such as repeating offending IP blocks, particular attacks coming from certain countries, or particular protocols being used improperly. By adapting to attack patterns, a protection service can harden itself against future attacks. There are 16 other types of DDOS attacks, so hang in there guys, they are doing the best they can.6 points -
3dxchat uses a combination of Cloudflare, Scalaxy, & Ispiria Network Solutions. The Cloudflare (USA) IP addresses are totally fine: 172.67.216.164, 104.26.1.90, 104.18.60.31 However, hackers are still able to freely access and DDOS attack: 5.61.57.85 (Scalaxy, Ispiria web host, Netherlands). This is the IP used to login to the game. Let's do some research on IP 5.61.57.85 - https://ipinfo.io/5.61.57.85 , which is associated with: ispiria.net / scalaxy.com Scalaxy has a bad reputation: https://scamalytics.com/ip/isp/scalaxy-b-v "Scalaxy B.V. is a high fraud risk ISP. They operate 6,136 IP addresses, almost all of which are running servers and anonymizing VPNs. They manage IP addresses for organisations including 3NT Solutions LLP, Internet Tekhnologii LLC, and ISPIRIA Networks Ltd. Scamalytics see low levels of traffic from this ISP across our global network, most of which is fraudulent. We apply a risk score of 82/100 to Scalaxy B.V., meaning that of the traffic where we have visibility, 82% is suspected to be fraudulent." Try visiting Ispiria or Scalaxy's web site. If you click Contact or Support, it doesn't show anyway to contact them, they're dead links. There's no phone number or anything. That's the sign of a terrible, cheap web host. That's your first problem. Web hosts like these are prone to hackers and DDOS attacks, because they're too cheap to get proper security which costs $$$. Doing a google search of IP 5.61.57.85, shows it has a history of problems: https://www.google.com/search?q=5.61.57.85 https://www.abuseipdb.com/check/5.61.57.85 https://cleantalk.org/blacklists/5.61.57.85 The IP 5.61.57.85 has a history of being used by forum spammers: https://raw.githubusercontent.com/ktsaou/blocklist-ipsets/master/stopforumspam_180d.ipset (look up 5.61.57.85 in this list) My recommendation is to call Cloudflare and ask them what web hosts they recommend; who can prevent DDOS attacks. They might be able to recommend a reputable web host in Netherlands. I hope the network/developer of 3dxchat sees this: 1. Your server should only communicate with Cloudflare IP addresses. That means the only IP addresses that are allowed to connect to it are from Cloudflare. Your server should have a hardware based firewall that rejects traffic from any other IP address other than Cloudflare. 2. 3dxchat client should only communicate with Cloudflare IP addresses. You can use Comodo to monitor 3dxchat IP address usage to ensure only Cloudflare IP addresses are being used. The whole idea is that your server only accepts traffic from Cloudflare, and 3dxchat only connects to Cloudflare. Cloudflare is the gateway, the gate keeper.6 points
-
5 points
-
I don't make conclusions like you or cpaadpro. That is the difference. I have no idea how "almost all" 3dxchat's futas/femboys look irl. I don't know what exact percentage of biologic males who claim to be transgenders in 3dxchat are really being ones and for which percentage it's just an ingame fantasy and irl they are just regular guys. The thing is – you don't have such a statistics as well. You only have personal experience, just as I am. But you for some reason feel entitled to make a conclusions about whole community using just your personal experience and thinking that it's a reliable data.4 points
-

Understanding what a DDOS attack is, and understanding mitigation isnt always easy
Xizi and 3 others reacted to Monique/Aurora for a topic
The Goal of the Attack: Sometimes referred to as a layer 7 DDoS attack (in reference to the 7th layer of the OSI model), the goal of these attacks is to exhaust the resources of the target. The attacks target the layer where web pages are generated on the server and delivered in response to HTTP requests. A single HTTP request is cheap to execute on the client side, and can be expensive for the target server to respond to as the server often must load multiple files and run database queries in order to create a web page. Layer 7 attacks are difficult to defend as the traffic can be difficult to flag as malicious. Application Layer Attack Example: HTTP Flood This attack is similar to pressing refresh in a web browser over and over on many different computers at once – large numbers of HTTP requests flood the server, resulting in denial-of-service. This type of attack ranges from simple to complex. Simpler implementations may access one URL with the same range of attacking IP addresses, referrers and user agents. Complex versions may use a large number of attacking IP addresses, and target random urls using random referrers and user agents. Protocol Attacks The Goal of the Attack: Protocol attacks, also known as a state-exhaustion attacks, cause a service disruption by consuming all the available state table capacity of web application servers or intermediate resources like firewalls and load balancers. Protocol attacks utilize weaknesses in layer 3 and layer 4 of the protocol stack to render the target inaccessible. Protocol Attack Example: SYN Flood A SYN Flood is analogous to a worker in a supply room receiving requests from the front of the store. The worker receives a request, goes and gets the package, and waits for confirmation before bringing the package out front. The worker then gets many more package requests without confirmation until they can’t carry any more packages, become overwhelmed, and requests start going unanswered. This attack exploits the TCP handshake by sending a target a large number of TCP “Initial Connection Request” SYN packets with spoofed source IP addresses. The target machine responds to each connection request and then waits for the final step in the handshake, which never occurs, exhausting the target’s resources in the process. Volumetric Attacks The Goal of the Attack: This category of attacks attempts to create congestion by consuming all available bandwidth between the target and the larger Internet. Large amounts of data are sent to a target by using a form of amplification or another means of creating massive traffic, such as requests from a botnet. Amplification Example: Honestly the list can go on and on for the specific types of attacks but to answer your question LeeLoo that's a strong possibility. And if that's the case, the attacker can continue attacking and overloading the system. Which is why it takes time to be able to find out what type of attack it is and once they know that they then have to track down the source but doing this takes a lot of time yet the 3dxchat team is making remarkable progress to get the game up n running. They really are doing the best they can. AND REMEMBER: . Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.4 points -

Third gender option for our avatars (Poll)
YenneferVengerberg and 3 others reacted to Xizi for a topic
To be honest I myself took a big part in it. And... It's kind of related to the topic. Because some people tend to use their rl views on the human gender (often a very wrong views) as an argument about how things should be in game. Like these proposals about mtf transgender avis be based on male body for example. So I don't agree that this discussion really unrelated. But yes... Better stop it. I hope at some point Gizmo and Lisa will read the discuss opened in this thread and will take one or another decision.4 points -
If you say you are a woman then you are a woman. I'm not saying you are not https://www.dictionary.com/browse/woman I don't see any reference to a womb being required for womanhood. What about women who were born without a womb, women who for whatever reason have lost there ability to birth children? Are they excluded? No longer women as you see it And what about men or intersex people who have wombs and can have children... Are they women to?4 points
-
Dear Tech Savey Players of 3dx
Sage Stoner and 3 others reacted to Xaufin for a topic
Authenticating logins before allowing sign-ins is one way. If you put a CAPTCHA type test on the login screen, you might shut down this attack altogether. That might be the easiest hot fix. It will inconvenience players, but it will also stop the server crashing (provided you've done it correctly). Since the problem is that the server can't process every request being received, the obvious answer is to stop processing them without authenticating them. For long term, it's best to use some type of middleware solution for protection, like AWS. The only other options are: Have a full-time network programmer who can code proprietary solutions himself Hire a temporary network consultant to either code the solution for you or advise the best approach. If you're doing none of the above things, 3DXChat could be dead within the month.4 points -
3DXChat Community! Due to the DDoS attack on the server, the hard disk was damaged, the system crashed and administrators responded slowly. User data was not affected, however, restoring the game in such conditions is difficult and long. Our plan is as follows: We have a new test server, which is located in a more respectable data center. We transferred all users to the test server to quickly give people the opportunity to play the game. Since the test server has not been fully tested, players will probably encounter bugs, which we will try to quickly patch to fix. Please bare this in mind and please continue to report them. We understand that playing in this way can be uncomfortable for many players, so we will freeze all current membership time until the situation improves, all registered users will play for free until it's solved. Known Issues: - Profiles issue (double click "My Profile" to fix it); - In rare cases, the login window may block you for 15 minutes; - Not all users who receive compensation have the opportunity to enter the game; - The ignore function does not work; - Incorrect display of colors in the chat; - Radio; - Incorrect display of clothes when leaving a closed room. First release: - Optimization of the server and client code. Resistance to load at rush hour; - The rooms stay open even if the owner has logged off the game. Will stay open until the last visitor leaves; - Server side random /roll (1-100), /roll1 (1-6) and /roll2 (1-12); - Protection of User Worlds (It is necessary to re-save the world); - Men's hairstyles. Future releases: - Bugfixes; - Women's hairstyles. - Poses. Future plans: - Moderation of User Worlds. The patch is already available. In order to update just run 3DXChat and the patcher will start. Please note: If the game is too unstable during testing, we reserve the right to suspend the server until the malfunction has been fixed. Bug Tracker: Report Errors Here Q: Patcher client freezes during update.A: You can download and install the latest version of the client (Build 421) from your personal account or via this link: https://mega.nz/file/JRJUiKiS#03hwmAXPb1IbQjIcmpo6pR0eqf6slvipRa1dnppXlhw Thank you for being with us during this difficult time!3 points
-

Understanding what a DDOS attack is, and understanding mitigation isnt always easy
VenomousVixens and 2 others reacted to Monique/Aurora for a topic
Well it's a good thing I didn't claim that the information came from me now isn't it? I simply copied and pasted cuz they explain it very clear and wonderfully simple. I apologize for your misinterpretation. I don't recall saying that they were my words but that's negligible because a perfectly reliable source was being copied and posted to help others understand exactly what it means Even though that's precisely why that information is accessible to the public anyways. But next time I'll make sure to cite my sources so know it alls don't feel the need to comment on such ridiculous posts. I didn't post it for smarta**es I posted it for other people who may be curious, confused or interested in what it is. No matter how I explain it id still be referring to a website or a textbook. SOURCES: What does know it all mean? Definition of know-it-all : one who claims to know everything also : one who disdains advice informal + disapproving : a person who talks and behaves like someone who knows everything : a person who always claims to know everything Know-it-all | Definition of Know-it-all by Merriam-Webster www.merriam-webster.com/dictionary/know-it-all3 points -

Understanding what a DDOS attack is, and understanding mitigation isnt always easy
Xizi and 2 others reacted to Monique/Aurora for a topic
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination. How does a DDoS attack work? A DDoS attack requires an attacker to gain control of a network of online machines in order to carry out an attack. Computers and other machines (such as IoT devices) are infected with malware, turning each one into a bot (or zombie). The attacker then has remote control over the group of bots, which is called a botnet. Once a botnet has been established, the attacker is able to direct the machines by sending updated instructions to each bot via a method of remote control. When the IP address of a victim is targeted by the botnet, each bot will respond by sending requests to the target, potentially causing the targeted server or network to overflow capacity, resulting in a denial-of-service to normal traffic. Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult. What are common types of DDoS attacks? Different DDoS attack vectors target varying components of a network connection. In order to understand how different DDoS attacks work, it is necessary to know how a network connection is made. A network connection on the Internet is composed of many different components or “layers”. Like building a house from the ground up, each step in the model has a different purpose. The OSI model, shown below, is a conceptual framework used to describe network connectivity in 7 distinct layers. While nearly all DDoS attacks involve overwhelming a target device or network with traffic, attacks can be divided into three categories. An attacker may make use one or multiple different attack vectors, or cycle attack vectors potentially based on counter measures taken by the target.3 points -

Website to see actual 3DXChat server status
SusanLouisa and 2 others reacted to Villanelle for a topic
wow a good idea, are you sure you're in the right place?3 points -

Third gender option for our avatars (Poll)
Xaufin and 2 others reacted to Ghost Girl for a topic
you can't define transgender in a third option because trans is more than one gender. Transmales exist along with transwomen and nonbinary and intersex. As much as I would love for trans representation the truth is, a trans girl is just a girl with male parts and a trans male is just a male born with female parts. So to do my trans sisters and brothers justice would be to be more inclusive. Accept trans women as women and trans men as just men. If there should be a third option it would be better to make a futa option and while I don't mind it, I would never want to restrict the penis option for women. So I can't back that idea either. The best idea I can think of would be a penis and vagina option for male and female avatars. In this scenario a trans woman could decide to have a penis or vagina and a trans male could also have the same option. So just leaving the two, female and male we could change the game to let the user decide what sex organs they would like. It makes sense to me currently, but I have had a few whiskey and cokes. So I will revisit this in the AM.3 points -
3 points
-
3 points
-

Build 420 (Test Server)
BillyBigWilly and 2 others reacted to Lisa for a topic
The server is running3 points